4/16/2024
Defense in depth is often deployed stealthily, so much so that in the physical world, it is often overlooked. It’s a principle from the physical world that is critical there and in cybersecurity.
Defense in depth is the idea that one can achieve more robust security by layering the defense mechanisms.

Three Physical Defense in Depth Security Examples
A few examples of layered security from the physical world may make the concept easier to understand:
Physical Barriers, and Surveillance & Guards

On my first visit to Washington, DC, I had to go by the White House. I noticed the fence, large yard, car inspections, gate guard, and rooftop snipers. Today, there are more layers of defense, including bollards in front of the fence.
In the case of bollards and the fence, the bollards are physical controls to protect against vehicles trying to ram through the fence. In contrast, the fence is primarily intended to prevent humans, motorcycles, and maybe horses from entering the grounds.
Around the District and other large urban areas, bollards can be seen in front of museums, office buildings, and parks. Retractable ones often protect driveways. Mostly unseen physical controls in DC (and most capital cities) are the many close-circuit security cameras, plainclothes guards, and motion or thermal alarm systems.
Visitor Management and Security Personnel

A few years ago, I was blessed enough to tour mainland China. One excursion on our tour was the Great Wall. Most people have seen photos or images of the Great Wall, but few know it contains Defense in Depth characteristics. While the Great Wall is a physical layer of defense, it has two other essential features.
One is the “notches” in the upper edge of the wall, known as loopholes. These allow archers to defend against marauders.
Another is more subtle: stairs to access the walkway along the top are uneven.
The risers on the stairs are of varying heights. That makes them very difficult to climb (been there, done that) – especially for an invading army. However, the Chinese armies defending the wall were repeatedly drilled on ascending and descending the stairs so they could do so efficiently and safely!
Bypassing Physical Controls

The third example of Defense in Depth is really an example of the lack of Defense in Depth. A frighteningly common tool by criminals in larger US cities is the “crash and grab” – a technique where criminals drive a vehicle through the front of a store to enter and burglarize the merchandise.
If you look at the first image in the linked article, you’ll see bollards designed to defend against such attacks. Sadly, businesses in vulnerable areas often only have metal lattices protecting their windows and doors but lack protective bollards.
Why Defense in Depth In Cybersecurity?
As in the physical world, cybercriminals may try different attack vectors against organizations. So, as in the examples above, having multiple layers of defense in case one fails is the difference between a typical security strategy and a solid Defense in Depth strategy. The concept is sometimes called “belt and braces” or “belt and suspenders.” While multiple defenses may seem redundant, they help ensure safety and peace of mind.
One best practice is to use a managed service security organization to provide essential protections. It is still critical, though, to have local defenses, perhaps as a part of the provider’s solution. The benefits of the layered approach cannot be overlooked.
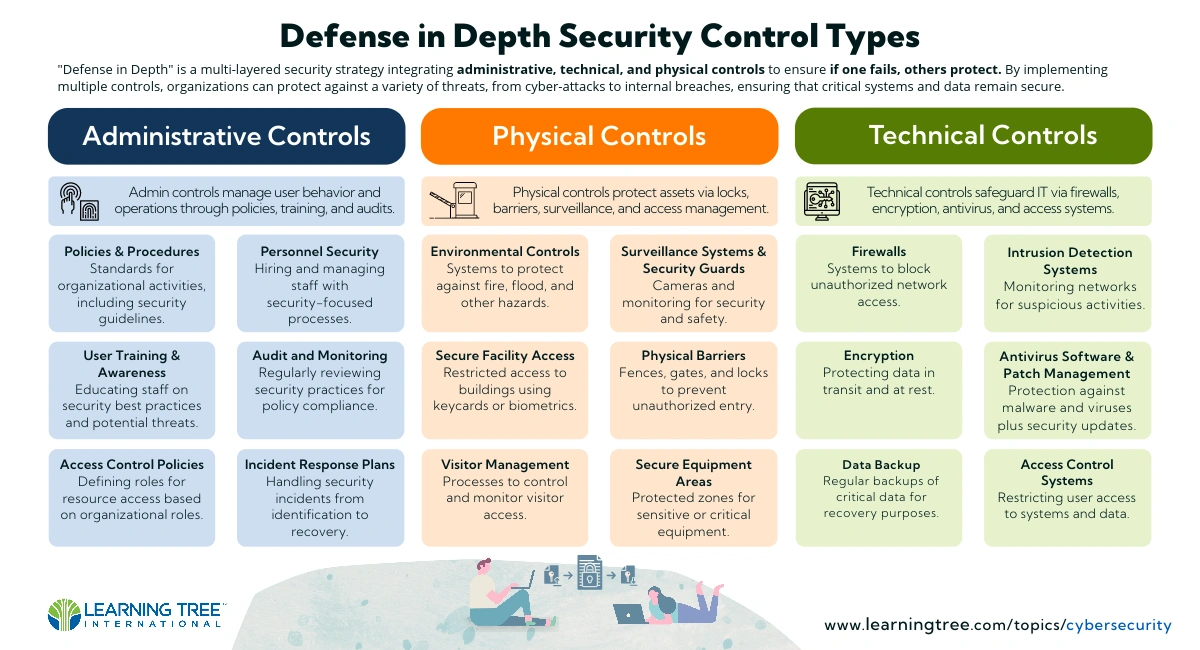
Technical controls such as a single firewall, antivirus program, intrusion detection system or other tool may be sufficient, but each is only one tool. If your single line of defense fails, nothing backs it up to protect you from a security breach.
As we discuss in Learning Tree’s Information Security Training course, the layers are critical to an effective defense. Sure, there is a higher cost for multiple layers, but the costs of a breach are likely significantly higher.
While the layers may seem invisible to users and attackers, they are effective defenses. As we all work to protect our organizations from increasing threats, it is essential to ensure that assets are protected by multiple layers to defend against the myriad tools attackers deploy.
Find more tools and information for building your Defense in Depth strategy in our Cybersecurity Resources.


