4/25/2018
For National Cyber Security Awareness Month, we are resharing some of our most popular cyber security blogs from the past year to ensure you are staying #CyberAware online - whether at home or in the office.
Maybe you've heard a little about the Certified Ethical Hacker or CEH exam. You probably have some questions:
What is a certified ethical hacker?
How does a CEH fit into an IT organization?
How do you get certified?
What knowledge and skills are crucial to success?
How does CEH relate to other cybersecurity certifications?

Let's take a look!
Ethical Hacking and Penetration Testing
I'm a practical guy. Rather than test details, I think first of what someone would do. To me, ethical hacking and penetration testing describe the same thing. It's an approved and aggressive attempt to exploit your own systems. It uses the sophisticated attack techniques. It provides the most complete analysis of cybersecurity risks.
But What About A Certified Ethical Hacker?

Now we're being specific! That's someone who has passed the EC-Council Certified Ethical Hacker exam. CEH is a significant step beyond the CompTIA Security+ certification, both in preparation and benefits. See the EC-Council page for full details.
How Does CEH Fit Into IT Organizations?
If you're with the U.S. Department of Defense, other agencies, or their contractors, CEH can be a formal requirement. Directive 8570.01-M specifies certification requirements.
The intro-level summary is to start with Security+. Then, do CISSP when you move to an advanced technical position or into management.
I only briefly mentioned the more advanced CSSP (or CyberSecurity Service Provider) specializations. There are five of them, and CEH is approved for four. So, CEH is often a second or third cybersecurity certification for more technical staff.
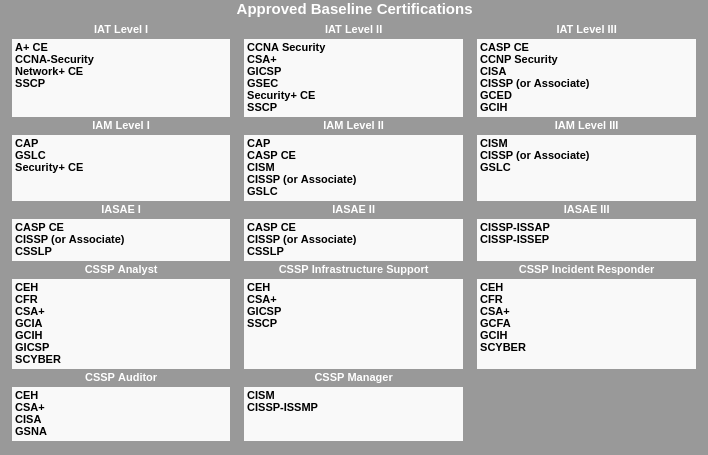
However, let's also be practical. The CEH requires you to know about a wide variety of tools. Organizations need people who can use those tools.
How Does CEH Fit Into Your Learning Tree Path?
Information Security Training, is an awareness and language class. You learn what threats exist, how to talk about them, and who does what.
For example, a security scan might warn of a buffer overflow vulnerability. A 468 student should know that's a common problem fixed by a software patch. System administrators apply patches. But, what if the vulnerability (or bug) is in software written in-house? Then your programmers must provide the patch.
CompTIA Security+® Training and the associated CompTIA Security+ exam have you recognize vulnerabilities from symptoms or descriptions. For example, your web application expects a user's name as input. The test sent a strange string with punctuation marks. The application revealed sensitive data. After course 446, you would recognize that as a SQL injection vulnerability.
CEH requires you to know how to run the scans and interpret their results. You must first find the symptom. It will not take the simplest possible form as it does in 468 and 446. CEH examples are more realistic. For example, can you find a real-world SQL injection attack contained within the payload of a Wireshark trace? Then you must diagnose the problem or specify its solution.
Learning Tree has two courses in the ethical hacking and penetration testing area. Here's my short take:
If you want to learn to do penetration tests, take Penetration Testing Training: Tools and Techniques
If you want to pass the CEH exam, take course 2031, {course 2031}
How Do You Get Certified?
The exam costs US$ 950, so you want to pass the first time!
EC-Council strongly recommends that you attend accredited training. For example, Learning Tree's course 2031, Certified Ethical Hacker (CEH) Training
It is possible to do CEH through self-study. However, EC-Council then charges even higher fees. They also require more paperwork, documenting relevant work experience or educational background.
The exam contains 125 multiple-choice questions. You have 4 hours to complete it. That means about twice as much time per question, compared to Security+. However, time management is at least as important. You must interpret much more complex data.
What knowledge and skills are crucial to success?
You need a solid background in networking. You need some background in server administration, both Linux and Windows. Programming experience will be helpful for understanding the exploits.
You need to know practical details about running and detecting exploits. For example, not just that DNS cache poisoning exists as a threat, or how to sketch out its concepts. Can you use it to redirect users to malicious sites?
You need to know how operating systems authenticate users and manage memory. Can you inject a Trojan and analyze its activity? Can you enumerate installed programs, services, and accounts on a Windows server?
An exploit might plant a backdoor using a shell bound to the DNS port. Do you know what attack tools would be involved, how to plant the backdoor, and how to detect it?
Specific CEH tools include Nmap, Wireshark, OWASP tools, Netcat, password crackers like John the Ripper, and wireless tools like Aircrack-ng and Kismet.
Multi-component toolkits include Kali Linux and Metasploit. You must analyze reports from vulnerability scanners like Nessus and OpenVAS.
Stay Realistic
CEH is a multiple-choice exam, not a practical exam. You won't run tools during the exam. You interpret sample output.
For most people, the volume of material in the CEH is somewhat overwhelming. Class hours will show what you need to know. You will need significant time outside class hours.
You'll take away the list of what you don't yet know. In the following days or weeks, you will get up to speed on what you personally need. This will almost certainly involve experimenting with some tools on test systems.
It's Tough!
If I had to pass the CEH within the next six months, I would definitely take Cyber Security Risk Assessment Training.
AUTHOR: Bob Cromwell
Related Training:
Cyber Security Training


